Common Squid Requirements - Part 2
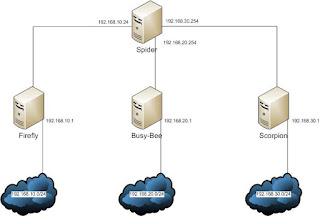
7. Set Maximum Download Size To set the maximum size of a file to be downloaded, the parameter reply_body_max_size can be used. The size is calculated in bytes . For example, if the maximum size of download is 50 MB (50*1024*1024 = 52428800), then here's how it is done- root@firefly:~# vim squid.conf #### Declaring the ACL #### acl our_network src 192.168.10.0/24 acl vip src 192.168.10.100 #### Applying the ACL #### #### Again, the sequence is important #### reply_body_max_size 0 allow vip #### the vip has no size restrictions #### reply_body_max_size 52428800 deny our_network #### no one in our LAN can download files larger than the limit #### root@firefly :~# squid -k reconfigure #### this command can be used to tune squid with last configuration without restarting #### 8.Setting Specific Time/Date for Internet Access The following lines have been taken from the ...