OSPF Simulation using Quagga
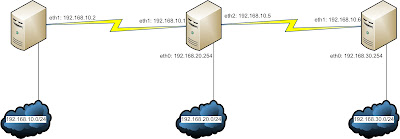
There's a newer version of this article available in my blog. Scenario IP Details All the Routers in the diagram are actually Debian Machines. Router Alpha: eth0: 192.168.10.254/24 eth1: 10.0.0.2/30 Router Beta: eth0: 192.168.20.254/24 eth1: 10.0.0.1/30 eth2: 10.0.0.5/30 Router Gamma: eth0: 192.168.30.254/24 eth1: 10.0.0.6/30 Objective We would be configuring the Linux boxes with dynamic routing protocol OSPF for total connectivity. This would be done with the help of Quagga. Router Alpha Configuration root@alpha:~# apt-get install quagga First, we have to enable the routing protocols needed. root@alpha:~# cd /etc/quagga/ root@alpha:~# vim daemons zebra=yes bgpd=no ospfd=yes ospf6d=no ripd=no ripngd=no isisd=no Next, we would be configuring the interface parameters. Keep in mind, there are example configuration files stored in /usr/share/doc/quagga/examples. root@alpha: